The link you clicked on was part of a phishing awareness campaign. Below is a presentation on the risks of phishing and some common traits to help identify phishing attacks.
The link you clicked on was part of a phishing awareness campaign. Below is a presentation on the risks of phishing and some common traits to help identify phishing attacks.
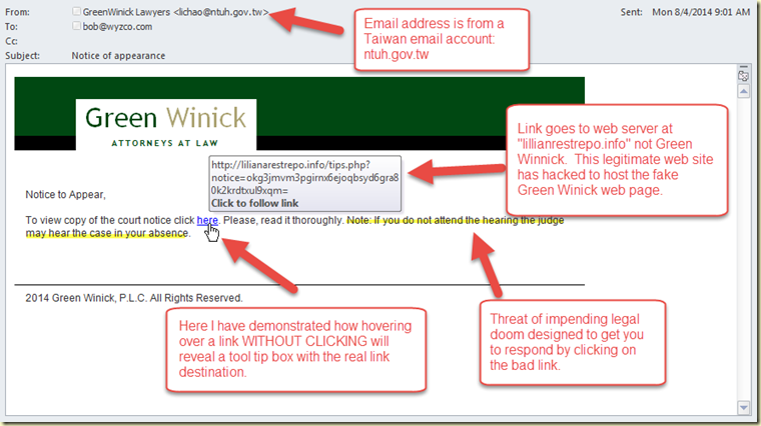
Phishing is still the overwhelming go-to choice for cyber-criminals launching an attack. Over 90% of computer system breaches start with a phishing email in an inbox. Finding ways to unmask these impostors is a good first step are protecting yourself from a phishing exploit. Let’s look at this first example, apparently from a law firm about a legal action.
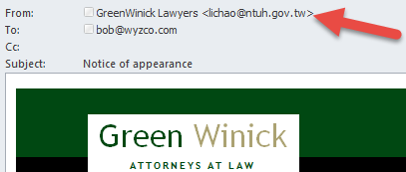
Spoofed sender – The first issue is that the sender is lichao@ntuh.gov.tw. This is undoubltedly a spoofed or worse yet hijacked email account. It obviously not from someone who works at Green Winnick.
Generic Greeting – Most phishing emails are sent in bulk to thousands, even millions of email addresses. The greeting will not be personalized for you, but something such as “Dear Customer,” or in this case “Notice to Appear.” Sometimes they may insert your email address on the greeting line. Though in the case of a spearphishing attack, the email will very definitely be addressed to you, because this email was specially created just for you after much research by the attacker.
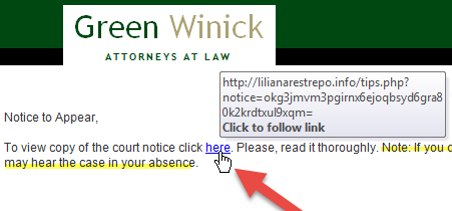
Bad Link – The link hiding under the word “here” does not go to a courts website or to Green Winnick. It is going to a website at lilianarestrepo.info. What follows the forward slash, and the long string of characters would indicate that this is an interior page that is probably carrying a drive-by download of malware. We were able to reveal the destination by simply hovering over the link without clicking. The tool tip box opened and let us check the destination of the link without danger. If this trick does not work, you can try right-clicking the link and choosing “Properties” or “Inspect” from the context menu. (Not left-clicking – that will take you to the malicious destination!)
The Story – There is always a story. In this case, it is the threat of losing a lawsuit you of course knew nothing about. Sometimes it is a lost, damaged or undeliverable package. Might be unpaid and past-due taxes, or a past due invoice. Or on the positive side, you might have been told you won a lottery you never entered. After a natural disaster, phish are sent that play on your charitable nature by asking for a donation. Or the widow of an African prince wants your help moving a pile of money illegally.
The Emotional Hook – The story is designed to change your emotional state from whatever is normal for you to one of fear, anxiety, concern, greed, or anger. Or you may feel a sense of urgency or impending doom. The email will try to get you to make a hasty and emotional decision. If you are having one or more of these feelings, take a breath, and thirty seconds to calm yourself and perform a reality check
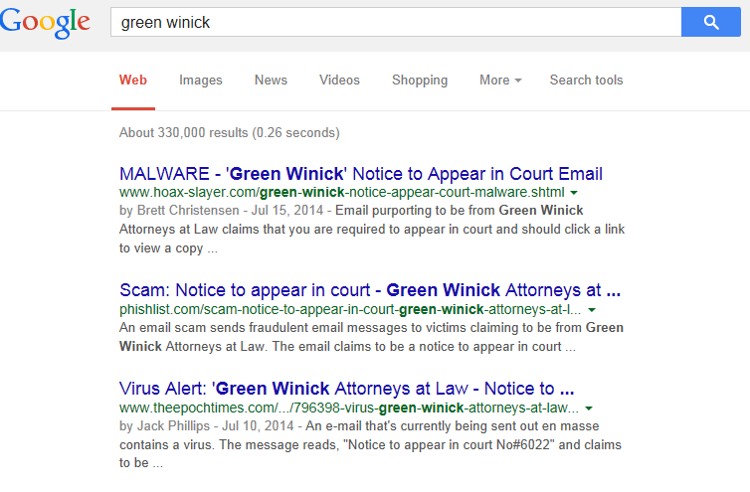
Google For Answers – When I googled for Green Winnick, I got the following results. This is pretty conclusive that the email is a fake.
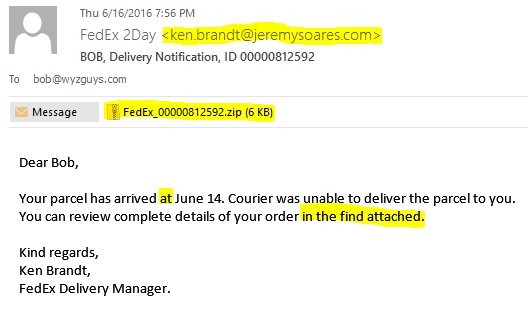
Let’s look at another example from “FedEx 2Day.” Here again we have the spoofed email address. Ken Brandt does not work for FedEx but is at “jeremysoares.com.” The greeting on this one is personalized, but they did it by popping off “Bob” from my email address. This time there is no link, instead there is an attachment.
The Attachment – Many phishing emails, especially the ones that are distributing the crypto-ransomware attacks, will appear with an attachment. Often, as with this example, the attachment is a ZIP archive which will contain a document or two and a malicious software program that will install when you unzip the attachment. Other common attachment types include PDF files, and Word, PowerPoint, or Excel documents. The Office documents may be using hidden macros (yes the macros virus is back!), although when you try to open the file you will be told you have to enable macros to view the file. They may even provide step by step instructions to help you! Enabling macros will run the Visual Basic software script and infect your computer.
Bad Grammar – For many of the people who craft these emails, English is not their first language. Bad grammar, poor sentence structure, and confusing language usage are another indication that this email may not be legitimate. To be fair to our adversaries, the English usage has improved dramatically over the last several years, so good grammar is proof of nothing.
The End Game – What are the bad guys after? It may be just enough to get you to open the attachment and start the malware infection. If you click through the link, you may be asked to provide your user ID and password, or other personal information on a web form. Often this link will take you to a page that is serving up a malicious drive-by download. Or this may be a scheme designed to part you from your money, as in a charitable contribution scam, advanced fee scam, or worse yet, using banking malware such as Everquest or DyreWolf to empty your bank account.
Hopefully this tutorial will help you wade through the minefield in your inbox, and avoid phishing emails. If you found this information valuable, I hope you will share this column with your friends, family members, or coworkers. As always, be safe out there!